In March 2020, I took CompTIA’s CySA+ (Cybersecurity Analyst) exam. Along with PenTest+, this bridges the gap between Security+ and CASP. In simple terms, PenTest+ is about “red team” activities (attack) whereas CySA+ is about “blue team” activities (defence). This certification was launched in 2017 as CSA+, but it was rebranded in January 2018 because someone else had already registered “CSA” as a trademark. The exam (CS0-001) stayed the same, although this was retired in October 2020.
NB The CS0-002 exam was launched in April 2020, giving a 6 month overlap, but this blog post covers the older exam. I noticed a bit of overlap between CS0-001 and PT0-001 (possibly because CySA+ launched first), so I’m guessing that CS0-002 will make them more distinct, but I can’t confirm that.
Thinking about the target audience for this certification, it seems to cover a hybrid role. Some of the objectives cover hand-on skills, e.g. configuring a firewall or doing forensic analysis on a PC that’s infected with malware. Other objectives are on the management side, e.g. risk assessments and data classification.
There are no formal prerequisites for this exam, but you should be familiar with the Security+ syllabus (even if you don’t have that certification). In my case, I’d already done Security+, along with similar content in SSCP, PCCSA, and SECFND (the first half of Cisco CyberOps Associate). So, I was actually quite glad to move onto more advanced content rather than repeating the same material over and over again!
I used 3 resources to prepare for this exam: 1 book and 2 Udemy courses. (These all contain some practice questions.)
- All-In-One Exam Guide, written by Fernando Maymi and Brent Chapman. I have reviewed this at Goodreads, including my errata list.
- Udemy course (Brent Chapman) This complements the book which he co-wrote, and I’d be happy to buy more videos from him.
- Udemy course (Jason Dion) I previously used his videos to prepare for ITIL Foundation and PenTest+, i.e. I’m already a repeat customer.
NB I read the first edition of the study guide. The same authors have written a second edition for CS0-002. The Udemy courses have been revised for the new exam, i.e. the new content replaced the original course at the same URL. As a fringe benefit, that means that anyone who paid for the old course can watch the new course (e.g. to recertify) without paying again.
As you’d expect, there’s a lot of overlap between these resources, since they’re all based on the same exam. I don’t think you need all 3, but each of them has some material which isn’t in the other 2. They’re not too expensive (since Udemy have frequent discounts and sales), and I don’t begrudge the time I spent on any of them.
On the other hand, there were some gaps that weren’t covered by any of the training I did. In particular, the exam asked me about regular expressions (aka “regexes”). The exam objectives don’t explicitly mention regular expressions, but they do mention log files, and a regex is an effective way to parse a log file. CompTIA published a blog post in August 2018 (5 Linux Skills You Must Master to Be a Cybersecurity Professional) and skill number 2 is regular expressions. Fortunately, I covered these in my undergrad degree, so I was ok. Looking at the SECOPS study guide (the second half of Cisco CyberOps Associate), it covers regexes briefly in chapter 3 with suggestions for further reading.
In practical terms, if you’re actually using a SIEM (Security Information and Event Management) tool on a day to day basis, you’ll probably be using regexes already: log files tend to be quite large, and you need some way to identify the important information. More generally, the exam is expecting you to have real world experience rather than just reading a book or watching a video. Likewise, if you want to do this for a career then don’t limit yourself to the exam syllabus: it makes sense to pick up extra skills.
I found it useful to read a chapter in the “All-In-One” book, then watch Brent Chapman’s video as a recap to find out which bits I’d forgotten, then I’d make notes on that (e.g. the 4 phases of the pen testing “kill chain”). Typically, the book would go into more detail than the video. For instance, they both talk about the difference between 1st/2nd/3rd generation computer languages, but the book also talks about the specific byte sequences for PE (Windows) and ELF (Linux).
As a sidenote, there are other resources which go into more detail about byte sequences, e.g. talking about the difference between big-endian and little-endian systems; that’s important for pen testing, but beyond the scope of CySA+.
The advantage of the videos is that they can demonstrate how to use various software tools, e.g. the macchanger utility. However, some of those demos were captured at low resolution, so the text was too blurry for me to read even when I viewed the videos in HD. (Hopefully this was corrected in the newer courses for CS0-002.)
I noticed some variation between the Udemy courses, e.g. Jason Dion demonstrates Maltego and Immersion (overlapping with his PenTest+ course) which Brent Chapman doesn’t. Similarly, Chapman showed the contents of his “jump bag” (various tools for forensic analysis); he mentioned write blockers, but didn’t show one. By contrast, Dion did show a photo of a write blocker in his course. That’s not essential, and you can get this info elsewhere, but I found it interesting. In Chapman’s videos, I particularly liked his description of the “Heartbleed” bug (using informal language).
Generally, I’d say that Chapman’s videos are more scripted, whereas Dion speaks “off the cuff”. However, Dion also seems to take the Calculon approach (from Futurama), i.e. he only does one take. That means that there are several videos where he makes mistakes and then corrects himself. There were also cases where Dion made mistakes without correcting them. E.g.
- In lecture 29, he said “netstat -0” (zero) rather than “netstat -O” (letter). This wasn’t simply a slip of the tongue, because the slide on the screen had the same mistake.
- In lecture 31, his description of the firewall config was wrong. A wildcard mask of “0.15.255.255” corresponds to a subnet mask of “255.240.0.0”, i.e. a /12 rather than a /16.
- In lecture 108, he says “TACACS” when the slide says “TACACS+”. They are significantly different protocols!
- In lecture 126, he says that we should install a new SSL certificate “or TLS because it’s better”. However, SSL and TLS both use the same X.509 certificate!
Those specific examples might have been corrected in the new version of the course. Since I spotted them, they didn’t do me any harm, but I’m more concerned about any (hypothetical) mistakes which I didn’t notice. There were some similar errors in his PenTest+ course.
As I mentioned above, I also spotted some errata in the All-In-One textbook, so this is a wider issue, and you should be wary about taking any information at face value (including this blog post). That’s also a benefit of doing a couple of different courses, so that you can pay particular attention to any discrepancies between them and then figure out for yourself what’s correct.
The actual exam is 165 minutes (2 hours 45 minutes), not counting the extra time to read the NDA at the start and do a survey at the end. I finished it in 1h45m, i.e. I had an hour left over, so I didn’t feel any time pressure. However, bear in mind that you can skip over questions and go back later. In particular, you might want to skip over the performance based questions on your first pass and just focus on the multiple choice questions (which should be quick), then go back to the performance based questions on your second pass; once you know how many there are, you can divide up the remaining time.
Some of the information in the questions is irrelevant. E.g. they might mention that a client is connected to a wireless network with a particular SSID, even if the actual problem is SQL injection on the website (i.e. it would also occur on a wired LAN). That reflects the real world, and you need to identify what’s important.
Some of the questions are objective, e.g. there is 1 statement which is true and 3 statements which are false. Others are more subjective, e.g. “In situation X, which of these actions would you take first?” Or “You have found several vulnerabilities in a system, which of these is the worst?” In other words, all the possible answers are worthwhile, but you need to pick which one is most important, and this is sometimes a judgement call.
When I was reviewing my answers, I noticed that one of the performance based questions was quite sneaky, i.e. the obvious answer was incorrect and I had to look carefully at all the clues that were provided. I don’t say that as a criticism: I was actually quite amused, and I sat there thinking “Well played! Nice try, but not good enough – I’m not falling for that.” Essentially, I viewed the person who set the questions as a worthy adversary.
The CySA+ certification is valid for 3 years, and it renewed my existing certifications (A+, Network+, Security+, PenTest+) at the same time. However, there seemed to be an odd glitch on the CertMetrics website where it added 3 years to their existing expiry date. I.e. the existing certifications will expire 5 years after my CySA+ exam rather than all the certifications (old and new) staying in sync:
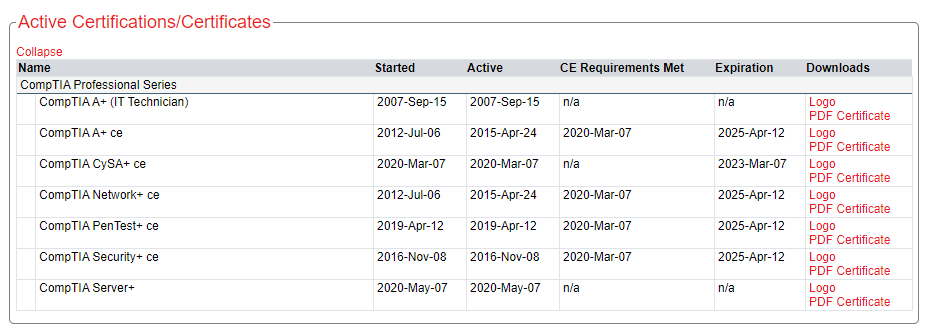
I contacted CompTIA tech support, and they said that this was correct. It doesn’t match their FAQ or past behaviour, but if they’re happy with this then my conscience is clear!
Passing this exam also gave me 2 stackable certifications:
- Security Analytics Professional (Security+ and CySA+)
- Network Security Professional (Security+, PenTest+, and CySA+)
I passed the exam on a Saturday, and Acclaim gave me the corresponding digital badges the following day (Sunday).