A while back, I was setting up an internal website (on a Windows domain with Active Directory), where I needed to identify each person who connected to it. IIS has an option for “integrated Windows authentication”: the idea is that if you’re already logged into the domain then you don’t have to provide a new username and password (or retype your Windows password) because the webserver will recognise you. This is similar to the way that permissions work on a fileserver, and I’ve used the same approach for desktop applications. One scenario is that you might want to use Outlook Web Access internally.
However, in order for this to work, the web browser actually has to send the relevant information to the webserver. The website doesn’t actually get your password, just your username, e.g. “example.com\john”. Opinions may vary about whether this type of authentication is a good idea; personally, I think it is, because I don’t want people to get into the habit of typing in their password whenever a pop-up dialog box asks them for it. Still, whatever your views, it makes sense to be able to control this setting.
In Internet Explorer, it should be enabled by default. Go to the “Tools” menu, then “Internet Options”, then the “Advanced” page, and scroll down to “Security” section. In IE7, it looks like this:
The relevant setting is “Enable Integrated Windows Authentication”, so you can tick it or untick it as you prefer, then restart the browser for this change to take effect.
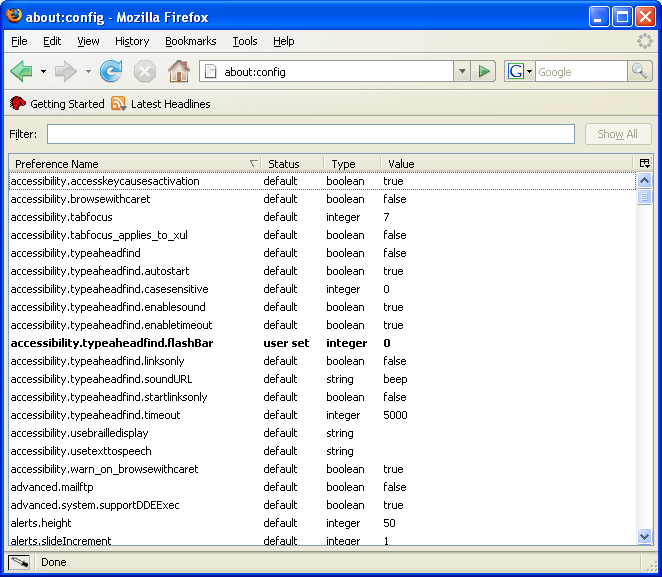
In Firefox, it’s a bit more tricky. By default, integrated authentication is disabled, so you get prompted for a username and password when you go to the website, and if you don’t enter them then you’ll get HTTP error 401.2. So, you have to type “about:config” (without the quotes) into the address bar, then you see a screen like this:
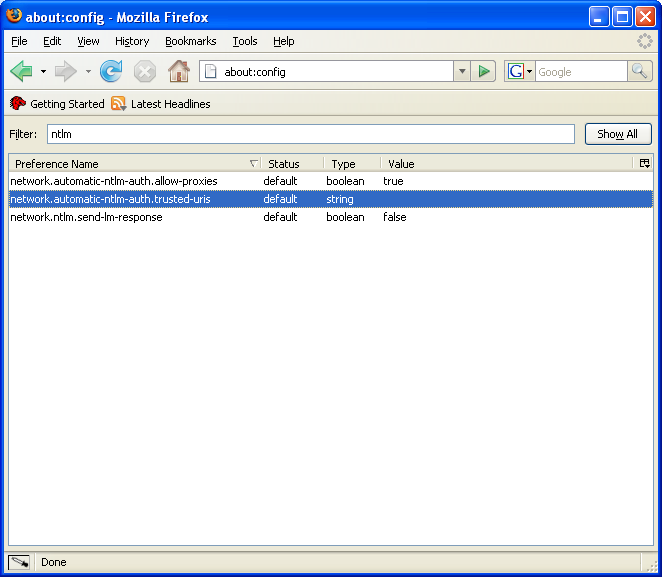
There are hundreds of settings here, so it will make your life easier if you filter the list. Type “ntlm” (without the quotes) into the Filter box, and you’ll see a much shorter list. The setting you want is “network.automatic-ntlm-auth.trusted-uris”:
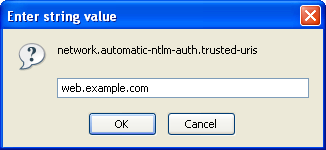
Double click on this (or press Enter) and you can specify the list of trusted sites:
You can either type in a full URL (e.g. http://web.example.com ) or just the server name (e.g. “web.example.com”). However, don’t put a trailing slash on the end. If you want to specify multiple servers, separate them with commas. You can match all the servers in a particular domain, but normal wildcards don’t work: you need to specify “.example.com” rather than “*.example.com”.
That’s all fair enough if you only have one machine, but it’s a bit of a faff if you have to deal with several machines on a network; these instructions are fiddly enough that I wouldn’t expect the average person to follow them. Even if they can, it’s a massive duplication of effort to ask 100 people to spend a couple of minutes on this, and it would be even worse on a larger network.
This is where Group Policy comes in. The idea is that you can specify various settings centrally, and then these apply to all people/machines in the relevant OU (Organizational Unit). Typically it takes about 30 minutes for these changes to take effect, but they don’t usually require people to log out and log back in again or to reboot the machine (unless new software is being installed).
I don’t think that there’s an option to enable/disable Integrated Windows Authentication centrally for IE. However, there is a related option for the security zones. The idea is that you have four zones (“Internet”, “Local intranet”, “Trusted sites”, and “Restricted sites”) in IE: you can specify which permissions should apply to each zone, and also which sites are in each zone. You can tell which zone you’re in by looking at the status bar (in the bottom right corner of your screen). For instance, while I’m connected to the LiveJournal website, it looks like this:
In theory, any webservers on the local domain should be in the “Local intranet” zone automatically, but I’ve found that this doesn’t always work. So, I’ve defined this centrally through Group Policy. I’ve put all of the staff accounts into a particular OU, and then the relevant section in GPO is:
User ConfigurationAdministrative TemplatesWindows ComponentsInternet ExplorerInternet Control PanelSecurity Page
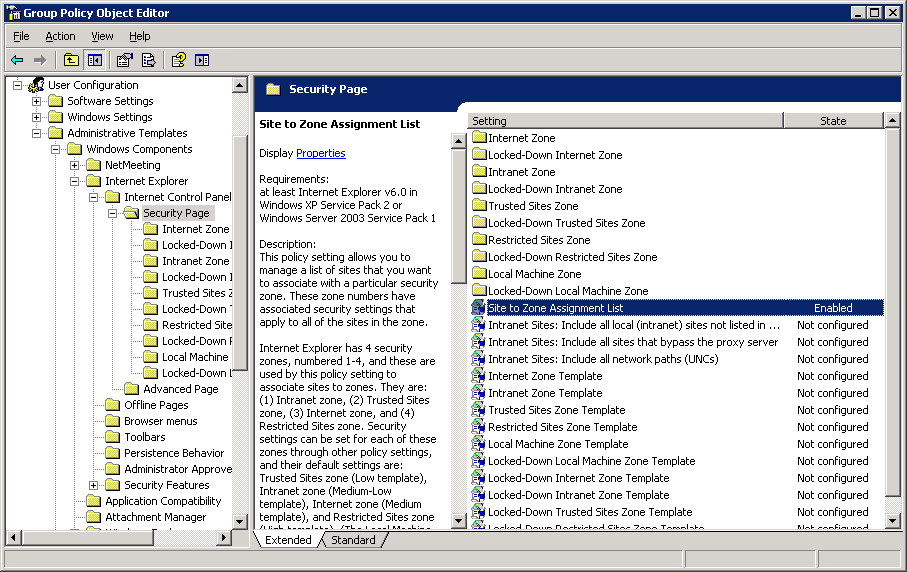
Then the relevant setting is “Site to Zone Assignment List”:
Anything that says “Not configured” means that it’s up to the end user to define their setting in the usual way. In this case, the setting is enabled, so you need to take a closer look at it:
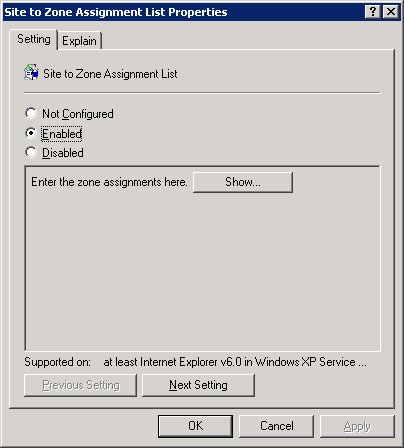
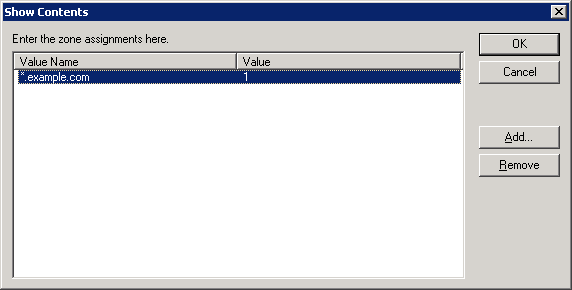
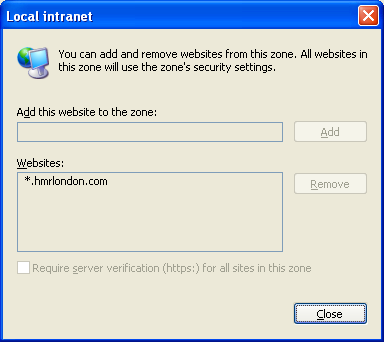
Clicking on “Show…”, you can actually define the sites:
Looking back at the description in the main GPMC (Group Policy Management Console), the value of 1 means that this site is in the Intranet zone.
One key issue to be aware of is that this setting applies to all the zones, not just the intranet zone. In other words, the list of sites for all other zones is now centrally defined to be blank. That’s not really a problem, because it probably makes sense for the IT department to decide which external sites are trusted, and if it’s safe for one user then it’s presumably safe for everyone else.
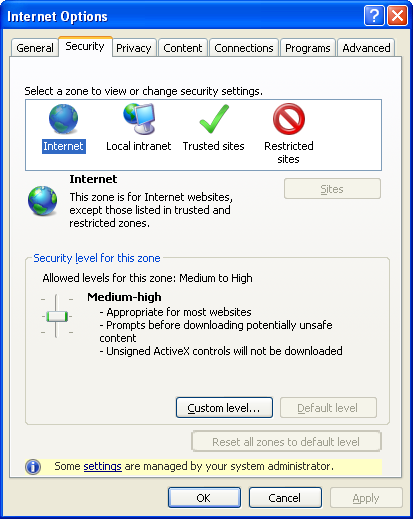
Back in Internet Explorer, it now warns me that some settings are managed centrally:
I can look at the list of sites for the “Local intranet” zone, but I can’t change it:
So, that’s all well and good. There are plenty more options available for Windows, and various applications (e.g. Microsoft Office) include their own templates which can be attached to GPO. For instance, I can specify which digital signatures are trusted (in order to enable/disable macros), and the applications will detect this setting. It would also make sense for me to define which security settings apply to each zone in IE (e.g. enabling/disabling ActiveX controls), and that’s on my “to do” list.
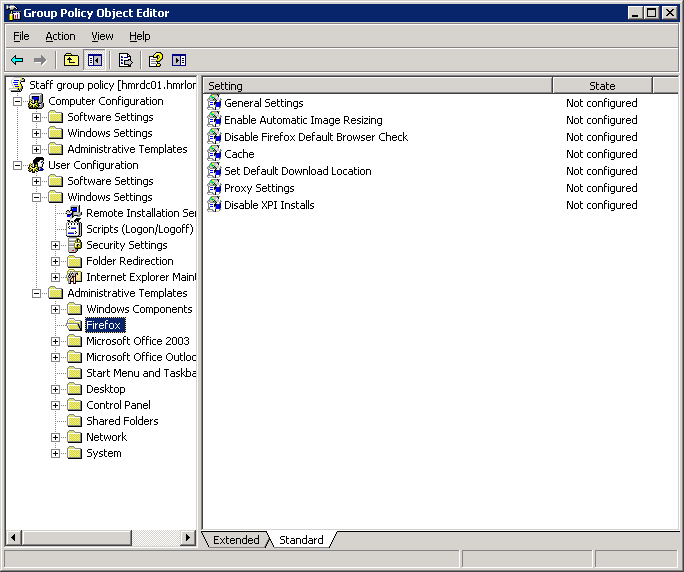
This brings me back to Firefox. Looking at the official website, I can’t find any admin templates mentioned there. This is a shame, but I did find a copy of “firefox.adm” on a different site; I don’t recall which one offhand. Adding this template to GPMC, it seems a bit limited:
I’ve put that in Standard view to make the screenshot smaller, but there are no descriptions for the settings in Extended view. There are only 7 settings, none of which are relevant to NTLM authentication.
In fairness, there are other templates available, e.g. this one at SourceForge (last updated in February 2005), but it could take me a long time to try them all out, eliminate duplicates, and identify which features each one has (and whether it actually works with the latest version of Firefox). And even if I do spend that much time, there’s no guarantee that I’d actually find a solution. Alternately, I could use a customised setup program, but that would mean re-installing it each time I want to manage a new setting.
The point of all this is that I simply don’t think Firefox is ready for corporate deployment. I have it installed on my own PC, and there are some situations where it’s better than IE, but it needs to allow central management if it’s going to become successful. I suspect that this is partly a philosophical issue, linked to the whole “freedom of choice” idea. However, I think it’s often best to limit choices.
Illustrating this with an anecdote, I remember a guy I went to university with. He was a year or two below me, and nowadays I’d refer to him as a “union hack”; he knew the constitution inside out, and a typical motion from him at a JCR meeting would involve modifying paragraph 8, subsection iv. That’s fair enough, and most of his changes were improvements, even if they weren’t urgently needed. However, there was one particular occasion when he came up with a motion that was extremely unpopular. We discussed it for a while, and it was blatantly obvious that he’d lose the vote on it, so he then came up with a new motion to dismiss the original motion. (Magic players and computer scientists will probably recognise the “stack” concept here.) The JCR President tried to dissuade him, saying that it would be easier just to let the original motion get voted down, but he was adamant.
So, we all had to vote on this new motion, and a lot of people were getting confused. We were all undergrads at a decent university (Durham), so it wasn’t a problem of intelligence, but the issue was just getting far more complicated than it needed to be. It was a bit like the Shrek 3 trailer: “Do you deny that you declined to rescind his rejection?” The guys sitting near me asked for my advice; I knew what they wanted (to get rid of his original motion), and they trusted me to tell them whether to vote “Aye” or “Nay”. In fact, either approach would work: they could reject both motions or just accept the new one. I guessed that most people would vote “Nay”, simply on the grounds that “Whatever that guy’s proposing, I’m against it”, so I told the people sitting near me to do the same; that way, they’d be on the winning side, and would trust my judgment in the second vote. The point is that they needed to choose a vote, even though both were ok.
There’s a similar issue if you’re navigating, and the driver asks which way to go at a turning. It may well be that either direction is fine, e.g. the roads merge again further on, but the driver still needs to go one way or the other, and he/she wants an answer quickly rather than a long explanation of local geography.
Coming back to computers, I’ve found that the same thing applies. People often ask me for help, and they don’t care about understanding what’s going on, they just want to know which button to click. So, I see it as my job to shield my end users from decisions as much as possible: if they don’t have to choose then they can’t make the wrong choice. I’m happy for people to select their own desktop wallpaper, but I will decide what’s best for security.