In April 2019, I took the Offensive Security Wireless Attacks (WiFu) course and the OSWP exam. (Along with PenTest+ and Microsoft 365 Fundamentials, this was my third exam in a month!)
NB This course was later rebranded as PEN-210, but this blog post refers to the older course.
In brief, I enjoyed this. I thought the content was interesting, and the exam was actually fun (similar to an escape room). However, the course material was written in 2014 and it could do with an overhaul; Offensive Security updated the OSCP in Feb 2020, so hopefully they will do the same for the OSWP at some point.
In particular, the course objectives include these:
- The student will learn to implement attacks against WEP encrypted networks.
- The student will learn to implement attacks against WPA encrypted networks.
- The student will learn alternate WEP and WPA cracking techniques.
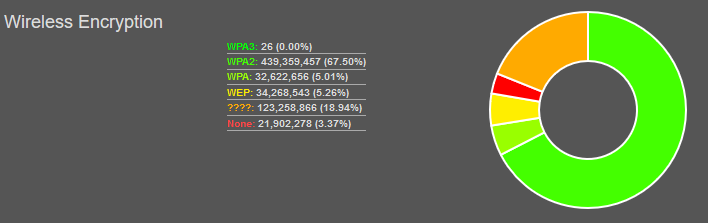
So, is this course/certification still relevant? How many people are actually using WEP/WPA rather than WPA2 (or open networks that don’t need cracking)? WiGLE (Wireless Geographic Logging Engine) has some stats on this. Here’s a snapshot from 2020-06-07:
In particular:
- 5.26% on WEP
- 5.01% on WPA
So, that’s about 10% of wireless networks. Based on that, I can see the skills being useful. However, when I scanned my local (residential) neighbourhood, I couldn’t find any WEP/WPA networks. Any new router from an ISP should come pre-configured with WPA2, and it’s been that way for several years now. I also wonder how up to date those stats are, i.e. whether the WEP networks still exist.
The good news (as a pen tester) is that the same attacks will work on WPA-PSK and WPA2-PSK. According to WiGLE’s stats, 67.5% of networks use WPA2, although unfortunately they don’t show a breakdown of Personal vs. Enterprise. If you’re using WPA2-Enterprise (802.1X authentication) then you’re safe against these attacks. However, in my anecdotal experience there are a lot of WPA2-PSK networks out there.
So, that’s a roundabout way of saying that yes, this exam is still relevant.
If you run a wireless network (at home or at work), how worried should you be? Before I did this course, I’d already heard that WEP is essentially worthless; now that I’ve experienced this from the attacker’s perspective, I can confirm that’s true. WPA2-PSK can be cracked, but it relies on a dictionary attack; if you’ve got a random passphrase then you’re pretty safe, e.g.
~*TJ8H|^u@<)Fk05Uq}t;5?N\v(bv<4s-nT`H””yA$(ha.bEP”+jEg)”&y({Fr
Equipment
Other pen testing courses involve VPN access to a lab network. However, the OSWP is different (due to the physical nature of radio waves), so you will need to set up a home lab to do the course exercises.
You might already have a machine set up to run Kali Linux, in which case you can continue to use that. However, I bought a new laptop to run Kali as a VM. In the longer term, I will hopefully use this for engagements. Looking online for advice, this is the best website I found: In search of the best Kali Linux laptop. (Other sites were more general, e.g. talking about the best spec for gaming, and I think their main goal was to earn commission on their links.) That site recommended an Acer Aspire, although the specific model they mentioned (the E 15) is no longer available so I opted for the A517-51P. That was in Oct 2018, and I think the model I bought has also been superseded; today’s equivalent is the Acer Aspire 5 Pro A517-51GP. This will cost about £700 (+VAT).
You will also need a wireless adapter and a wireless router, and the Offensive Security website has some recommendations:
Recommended Wireless Network Routers
- D-Link DIR-601
- Netgear WNR1000v2
Recommended Wireless Cards
- Netgear WN111v2 USB
- ALFA Networks AWUS036H USB 500mW
You might wonder why this is necessary. After all, my laptop already has a built-in wireless adapter, and I have a wireless router that I use for internet access. However, you will need to put the wireless network adapter into monitor mode (similar to putting a wired network adapter into promiscuous mode), and not all devices actually support that.
On the router side, I don’t really want to reconfigure my live network; I’d rather just have an isolated WLAN without internet access. Similarly, if you share a household with other people, they’ll probably get annoyed if you keep changing the settings on the main router and blocking them from the internet! Also, some of the lab exercises involve WEP, and you might find that some new routers no longer even support that as an option.
Unfortunately, the recommended devices are quite old, so you will need to look at the second-hand market. I bought a Netgear WNR1000v2 router (aka the N150) from eBay for about £13, and an Alfa AWUS036H adapter via Amazon Marketplace for about £24.
On the whole, these worked well. However, I couldn’t run the KoreK (chopchop) attack in my lab. It said:
"Failure: the access point does not properly discard frames with an invalid ICV - try running aireplay.ng in non-authenticated mode instead."
SaltwaterC had the same problem (using the recommended hardware), and wound up creating a soft AP instead. In fairness, the handbook and video does say that this attack won’t work on all APs. However, it’s odd that they’d recommend hardware which isn’t compatible.
You will also need “victim” devices connected to your test WLAN, so that they can generate traffic for you to eavesdrop on. Ideally you would use a device with a command line (rather than an iPhone), e.g. so that you can set up a continuous ping. I agree with what nickjvturner wrote:
“As for the Victim device, I started with a WinXP virtual machine running on the same host laptop as Kali Linux, this proved to be a little confusing. I was constantly switching between Kali Linux for attacks and Victim machine to view the effect, (mostly dropped pings). I recommend using a physically separate computer as the Victim if possible.”
In my case, I used a Windows tablet.
Prior study
According to the course overview:
“Offensive Security Wireless Attacks (WiFu) introduces students to the skills needed to audit and secure wireless devices. It’s for penetration testers who have completed PWK and would like to gain more skill in network security.”
I went straight to the OSWP, because it was shorter and cheaper than the OSCP. (In my defence, they’ve updated their website in the past year; it didn’t say that when I signed up.) So, the good news is that you don’t need to do the OSCP first.
However, it will be useful to have some familiarity with Kali Linux. I read through the (free) “Kali Linux Unleashed” book, which I’ve reviewed over at Goodreads.
If you’re going to use Kali Linux for penetration testing (particularly for the Offensive Security training/exams) then this book is a good place to start. However, the focus is a bit odd. Early chapters walk you through the process of downloading the .iso file from the official website and booting off a USB stick, then later chapters talk about how to compile your own custom version of the kernel!
I think the author should have swapped around chapters 5 and 6, i.e. explain how man pages work before referring to them for further reading. I got really bogged down in chapter 8 (package management) so my advice is just to skim read if you get stuck; don’t worry about memorising all the commands, just have a vague awareness of what’s possible so that you can refer back to it later if necessary. However, I don’t recommend stopping partway through the book, because there’s some important advice in later chapters (e.g. live persistence).
There are a few typos, e.g. “files ystem” rather than “file system”. However, none of them change the meaning of the sentence and as far as I can tell all the technical info is correct.
There is a corresponding exam: Kali Linux Certified Professional (KLCP). However, that’s currently unavailable (due to the COVID-19 pandemic), and it cost $450 when it was available; I didn’t take that, and you definitely don’t need that as a prerequisite for the OSWP.
The CWTS was useful, since I had a good grasp of wireless theory, but it’s not essential; as long as you understand basic network principles (e.g. the Network+) then I think this course covers everything you need to know. If some of the theory is new to you, you’ll need to make more of an effort in the first few chapters of the book, which are a bit dry.
The course
With other exams, I’ve normally arranged my own training (e.g. a textbook or a Udemy course) and then booked the exam separately, but with Offensive Security the training and the exam are a package deal. It costs $450 (roughly £350 in April 2019) for the course and exam combined.
On 2019-04-11 (a Thursday), I registered on their website and paid for the course. I had some trouble getting it to accept my credit card details, but I think they’ve now resolved that problem; everything went smoothly when I signed up for the OSCP today. I then had to wait a couple of days, and I received some emails on 2019-04-13 (Saturday morning) with links to the course materials: a pdf (386 page book) and a set of videos (roughly 4 hours in total).
NB Those links were only valid for 72 hours, and they’d charge me $100 if I wanted to download the material again (e.g. if I missed the window or if my hard drive failed and I lost my local copy). So, don’t sign up for this course just before you head out on a camping holiday! Also, make sure that you take a backup copy (e.g. on an external hard drive).
You have to take the exam within 120 days of that email arriving, i.e. the clock starts running once you have access to the course materials. If you miss that deadline, you’ll need to pay $150 to retake the exam. However, that should be more than enough time.
Obviously everyone’s circumstances will be different. It’s not a race, so don’t worry whether you take more or less time than anyone else. However, just as a rough guide, I took the exam on 2019-04-29 (Monday), so that was roughly 2 weeks after I got the material. I studied for this exam while I was between contracts, but I didn’t spend all day every day on it. In particular, I did the Microsoft 365 Fundamentals exam 2 days before the OSWP exam (i.e. I was preparing for both exams at the same time).
As another example, Andy Gill said:
“I was able to do all of the exercises and videos in a weekend. Having recently passed OSCP I opted to book the nearest date I could for my OSWP exam, roll on 1 week later exam time was upon me.”
Digressing into a bit of history, Kali Linux was previously known as BackTrack Linux (until 2013). The course material for OSWP is based around BackTrack, and they will give you access to a BackTrack machine in the exam. However, I chose to use Kali Linux (2019.1) for the lab exercises, on the basis that this is what I’ll use for a real world engagement, so I need to know how to actually carry out the same tasks on a more modern platform. Most of the time, that was fine, but I came across a few problems. As I said above, I’d like to see Offensive Security update the syllabus to run on Kali Linux.
The content refers to WEP and WPA, and those haven’t significantly changed since 2014. There have been amendments to the 802.11 standard, e.g. 802.11ac supports 80 GHz channels and faster speeds, but the 4-way handshake remains the same. As I said above, all of the attacks against WPA-PSK will also work against WPA2-PSK; there are differences between WPA and WPA2 (e.g. TKIP vs. CCMP), but they’re not relevant here. I haven’t used WPA3 yet, so I don’t know how that compares. (It’s outside the scope of the current OSWP exam, but maybe an overhaul will include that?)
Also, the pdf contains a table of contents. As a minor suggestion for improvement, it would be nice if those entries were hyperlinks, so that you could jump straight to the relevant chapter rather than navigating by page number.
The handbook and videos complement each other, which is a charitable way of saying that you need to hop back and forth between them. E.g. on p255 they start using variables (e.g. $AP) rather than explicit MAC addresses; there’s a video which explains how to set these up in .bashrc, but the handbook doesn’t mention that, and it’s just luck that I happened to watch the video before I read the relevant page. I wondered whether this was the try harder mindset in action, but I don’t think it’s deliberate.
In chapter 9 (p251), both figures are missing the bottom line, i.e. they don’t include the result. In the forum, someone else reported the problem in Nov 2012, so it’s disappointing that nobody at Offensive Security had corrected it in the following 6 years, especially when the course was overhauled in 2014. You can use other sources to fill in the blanks, but this suggests apathy rather than a deliberate design choice.
One benefit of the videos is that I saw them demonstrate the same command (as written) successfully; if it failed on my machine then I could assume that this was because I was running Kali Linux, rather than the pdf having a typo. The videos also mentioned the “macchanger” utility which isn’t in the pdf.
When I did the exercises, the main benefit was to get hands-on experience with the various tools. However, when things went wrong, this was also valuable, because I needed to really understand the theory in order to troubleshoot. (In my opinion, this is what separates a true penetration tester from a “script kiddie”.)
For instance, there was a situation where I captured a 4-way handshake (between a victim machine and the access point) then I ran aircrack-ng against the capture file. However, it said “KEY NOT FOUND”. I manually appended my PSK to the end of the wordlist and tried again, but I got the same result. I then tried a wordlist where my PSK was the only entry, and I still got the same result.
At this point, I turned to Wireshark. When I examined the capture file and filtered on EAPOL, I had packets 2 and 4 for each handshake (client to AP); I sometimes got packet 3 (AP to client) but I never had a copy of packet 1 (AP to client). The root cause turned out to be a configuration issue: my attacker (Kali) and victim (Windows) were both connected at 54 Mb/sec, but the AP was set to use “up to 150 Mb/sec”. When I changed the AP’s mode to be “up to 54 Mb/sec”, the problem went away (although I still got a couple of partial captures before a full handshake).
Aside from the speed issue, this gave me a new step for my methodology: I should verify the packet capture before I try to crack it. However, there are situations where I can’t use Wireshark (e.g. in the exam when I’ll only have a command line without a GUI). In that situation, I can use tshark instead (the terminal based equivalent). Here’s the command for Kali Linux:tshark -r MyCapture.cap -Y eapol
If this problem occurred during a real engagement, I assume that I wouldn’t be allowed to reconfigure the client’s access point! So, I’d need to have an alternate network adapter that matched their speed. Unfortunately, I haven’t come across a b/g/n adapter that works in monitor mode, but I’ll keep an eye out.
Hiccups
As I mentioned, some commands don’t work the same way in BackTrack and Kali Linux. Here are the issues I came across (and my workarounds), in case it saves anyone else some time.
In chapter 5, the grep SSID command doesn’t return any results. I had to put double quotes around the search term, i.e. grep "SSID" worked.
Section 8.3 (p228) says that you should run aircrack-ng -z to use the PTW attack. However, when I run the command in Kali Linux without any parameters (to get a list of options), it doesn’t list -z. The wiki says that this is the default from v1.0 onwards.
In chapter 13 (p299), the link to Cowpatty is broken. It currently says:
http://www.willhackforsushi.com/Cowpatty.html
Going via the top menu on that website, it should be:
https://www.willhackforsushi.com/?page_id=50
However, that page was last updated in July 2009, referring to coWPAtty 4.6. A better link is:
https://www.kali.org/tools/cowpatty/
That page refers to v4.8.
This brings up a more general point. Links to external websites are always hostages to fortune, because they’re outside the author’s control. However, when Offensive Security actually have a link on their own website, they should be using that instead! In fairness, looking at the change log on GitHub, nothing changed between 2009-07-03 and 2018-06-03.
Similarly, p301 of the pdf says that we should specify non-strict mode (-2) “as coWPAtty has an an issue with Airodump captures”. However, v4.8 doesn’t support the -2 parameter. It worked fine with my packet capture, so presumably that bug has been fixed.
Chapter 16 mentions airgraph-ng, but it’s not installed in Kali Linux. The wiki page was last updated on 2010-05-23, so I’m guessing that this tool is obsolete. This won’t be relevant in the exam (given the GUI element and GPS requirement), but it’s potentially useful in the real world.
I found a glitch in aircrack-ng 1.5.2 (issue #2002). If it can’t crack the key from a 4-way handshake, it just sits there. If you press Ctrl+C, it says “Quitting aircrack-ng” but doesn’t actually quit. So, you have to close the terminal window. This version of aircrack-ng was released in Dec 2018, so BackTrack (in the exam) used an older version without this problem. The bug has now been fixed so if you’re on Kali make sure that you get version 1.6 (released in Jan 2020). So, this just unfortunate timing for me, doing the course in April 2019 while the bug was active.
In the lab exercises, I used tshark to verify a packet capture. However, the version that came with BackTrack uses “-R” rather than “-Y”:tshark -r MyCapture.cap -R eapol
The exam
As with most exam providers, you have to arrange a date/time in advance. In my case, I scheduled the exam on 2019-04-25 (Thursday) for 2019-04-29 (the following Monday).
This exam is done from home (or your workplace), not at a test centre. It’s “open book”, and there was no online proctoring as such (i.e. nobody was watching me via a webcam), although they might have been monitoring my network activity.
Most of the other exams I’ve done have been multiple choice; a few involved some simulations. This was very different. The basic concept is that Offensive Security have a laptop sitting in their office, within range of 3 wireless networks. They will give you remote access to that laptop (IP address, username, password) so that you can connect via SSH. Once you log in, you will have a BackTrack Linux command line with all the relevant software installed (such as the aircrack-ng suite). Your job is to get the key for all 3 wireless networks within 3h45m. It’s that simple, and yet that complicated!
One concern I had was that I’d lose time waiting for tasks to complete. In multiple choice exams, it’s all on me: I answer the question, then move on to the next, and the only delay is my thinking time. However, if I’m doing a packet capture then I can choose how long I want to wait: the more IVs (for WEP), the better my chances of cracking the key, but the longer it will take. Similarly, I can adjust my options for a brute force attack, but the more things I try, the longer it will take. Fortunately, this wasn’t a problem. They provide you with sufficient resources (e.g. word lists) to complete your tasks in a reasonable amount of time.
Aside from cracking the networks, you also need to write a report, documenting the steps you took and the end result. This report has to be submitted within 24 hours of the end of the exam.
NB Once the exam is over, you no longer have access to the remote machine. If you realise that you forgot to write down a particular configuration setting, that’s too bad. In practical terms, that means that you need to make contemporaneous notes (i.e. write stuff down as it happens).
If you’ve done all the lab exercises then this should be pretty straightforward. You don’t need to memorise all the parameters for various commands, but you should have a conceptual understanding of what’s possible, i.e. what you’re trying to achieve. You can then look up the specific syntax in your course material.
The remote machine is running BackTrack Linux; your local machine can run any platform, as long as it has an SSH client installed. You are also allowed to have multiple simultaneous sessions, in the same way that you can open multiple terminal windows on a local installation. Some people (e.g. Mike Bond) recommend using the screen utility in Linux. Personally, I used a Windows desktop, with multiple instances of PuTTY. I then had Word open on a second monitor so that I could type up my notes and paste in screenshots as I was going along.
In my case, it took me about 90 minutes to crack all 3 networks. That meant that I could finish my report while I still had access to the remote machine. So, I effectively started over: if I’d just logged in, with no prior knowledge, could I use my report to reproduce the same results or had I missed anything out? I found a couple of mistakes while proofreading, so this was worthwhile. It took me another hour to write the report (i.e. 2½ hours in total).
The final step was to submit the report, and Offensive Security have strict instructions about this. I’m not kidding! At the time of writing, their instructions say:
- Your exam report is in PDF format
- Your PDF has been archived into a password-protected .7z file
- You used your OSID as part of the name of your .7z file
- You have uploaded your .7z file to https://upload.offsec.com
- You have emailed the link from the upload page to “oswp AT offensive-security DOT com”
NB These might change later, so make sure you check the current rules when you take the exam.
Suppose that you did everything right during the exam, but then sent “report.pdf” to their email address. They wouldn’t email you back and say “sorry, that’s the wrong format”, you would just fail the exam and have to pay $150 for another attempt. Looking at the forums, I believe some other people have made that mistake, so I was determined not to let that happen to me. Once I’d finished the report, it took me about 30 minutes to jump through the final hoops of renaming it etc., then double and triple checking that I’d got everything correct before I sent it in. However, even with all that, I still finished the exam early.
Aftermath
With a multiple choice exam, you get the result on screen immediately. In this case, someone had to manually review my report, so it took a bit longer.
You should get a reply within 12 hours, confirming receipt of your attachment. (In my case, it came 6 hours later.)
NB This email explicitly said that they hadn’t checked the format yet, so they were just confirming that my email had got through to them with the attachment intact.
After that, I was told that I’d get an email within 5 business days telling me whether I’d passed or failed. (Looking at the website now, I see that they’ve increased that to 10 working days, possibly due to the pandemic.) I actually got my results the following day (Tuesday evening UK time, Tuesday workday US time), and I passed, so that was good news.
After that, I got an electronic copy of my exam certificate by email, and they posted me a paper copy about 3 weeks later. I also have a digital badge for this in my Acclaim Credly profile.
(ISC)2 CPE
When I took the exam, the Offensive Security website said that it was worth 10 CPE points at (ISC)2, i.e. it would count towards the requirements to maintain my SSCP certification (20 CPE points per year). However, I can’t find that equivalency statement now, after the website was redesigned. Technically, CPE is awarded for study time, i.e. the course rather than the exam. However, the exam is counted as evidence that I actually paid attention during the course.
There’s no automatic data transfer between the organisations (unlike the Acclaim badge). Instead, I had to make a manual submission. This was a bit tricky, because the OSWP didn’t quite fit into the existing categories.
I logged into the CPE dashboard, and entered the dates for the course:

They asked “Have you fulfilled a CPE offered by (ISC)2” and I said “No” (because this came from Offensive Security). Then they asked for a CPE type. My initial thought was “Professional Development”, but I think that’s for non-security activities (e.g. taking a course on public speaking). Instead, I chose “Education”, then “Education Courses and Seminars”, then entered the details of the course:

NB The course name is “Offensive Security Wireless Attacks”, whereas the certification is “Offensive Security Wireless Professional”.
Next, I had to choose the domains, which was a bit of a judgement call. In Darril Gibson’s SSCP textbook, he maps chapter 8 (which includes pen tests) to these 3 domains:
- Networks and Communications Security
- Systems and Application Security
- Risk Identification, Monitoring, and Analysis
However, I don’t think that “Systems and Application Security” is relevant here, because I only went after the network infrastructure. On the other hand, I do think that “Cryptography” is relevant, since I need to understand a bit about how wireless encryption works.
Ideally, I think that any “pre-approved” CPE should have all of this documented somewhere, although that’s up to the (ISC)2 rather than Offensive Security.

Finally, I just had to review what I entered, and click “Submit”:
(ISC)2 accepted this, although that might just be because I never got picked for a random audit. Either way, I’m satisfied that this course/exam has continued my professional education.
Leave a Reply