When I created accounts with Facebook and LinkedIn, both websites asked me for my email password to help me find people I know. The idea is that they can log into my email account, go through my address book, then search their own database for people with matching email addresses. That would certainly be convenient, and save me some time, but I think it’s a very bad idea.
This goes back to what I said last year about logging into Windows as a standard user rather than an administrator. If you run a program, it can do everything that you can do, including things that you may not like, so it’s prudent to limit that access.
Here are some things that a malicious user/program could do with your email password:
- Send out spam messages from your account to everyone in your address book.
- Read through all your stored emails (the ones you’ve sent and received) and make a copy of them.
- Change the password on your account, thus locking you out.
- Try to use the same password on other websites.
- Go to other websites and click the “I’ve forgotten my password” button. Those websites would then reset your password and send the new password to your email account, which this other person now controls.
- Get access to a corporate VPN, e.g. all the sensitive data stored on a file server or in a database.
This may sound like paranoia, but there are precedents.
I started getting spam from someone I know last year, where the messages were bordering on obscene. I’ve set my spam filter up to trust people in my address book, so he was effectively “whitelisted”. This happened several times, but it stopped when he changed his password, which implies that it was an external source logging into his account rather than malware on his computer. In that situation, I think someone had just guessed his password, but if you give it away then they don’t have to guess.
Earlier this year, there was a targetted attack against HBGary, as reported at ArsTechnica. Quoting from page 2: “Neither Aaron nor Ted followed best practices. Instead, they used the same password in a whole bunch of different places, including e-mail, Twitter accounts, and LinkedIn.” I’m sure there are plenty of other people who do the same thing, to reduce the hassle of remembering several different passwords. On page 3 of the article, it says that people impersonated one of the victims by sending email on his behalf, pretending that he’d forgotten his username/password for the VPN. Once the attacker had that info, they could log in as him and do more damage.
In other cases, it would be even easier. For instance, if you use Outlook/Exchange on a Windows network then you don’t have to provide a separate password to get at your email; it recognises your Windows login. If you then want to log into your email remotely (OWA) then you enter your Windows username and password. If you have access to the VPN, you would use exactly the same username/password for that. Some companies will put an extra barrier in the way, e.g. a SecurID fob that provides a new code every minute, but not all. Bear in mind that LinkedIn is specifically aimed at corporate users
In fairness, LinkedIn say: “We will not store your password or email anyone without your permission.” However, do you trust them? That may not necessarily be a lie, but what if one of the developers there has stuck an extra line into the code somewhere; would anyone else have spotted it? Again, there’s precedent for this: the shareware app “G-Archiver” was stealing everyone’s passwords, and it took a long time for anyone to notice, even with access to the code.
Still, let’s suppose that we give Facebook and LinkedIn the benefit of the doubt, and assume that they are completely trustworthy. What they’re doing is still wrong, because it encourages people to pick up bad habits and ignore security policies. For instance, Yahoo say: “You are responsible for maintaining the confidentiality of the password and account, and are fully responsible for all activities that occur under your password or account.” Similarly, Google say: “You agree and understand that you are responsible for maintaining the confidentiality of passwords associated with any account you use to access the Services.”
Facebook and LinkedIn are weakening that message, by saying “Well, normally it’s a bad idea to give your password away, but it’s ok here.” This then implies that there are other situations where it would also be ok, which makes people vulnerable to phishing attempts, e.g. giving your password to someone who claims to be from your bank. Since they have demonstrated such a cavalier attitude towards security, I think that’s a big warning sign about the rest of their service. I still use both websites (for now), so I’m not saying that you should veto them altogether, but be cautious.
What’s also annoying is that there’s a better way of handling this: OAuth. It’s specifically designed for this situation, so you can give access to (some of) your data without handing over your password. Google support it, and hopefully other email websites do too. More info here:
OAuth: A Valet Key To Your Contacts
The password anti-pattern
However, if OAuth isn’t available, you still shouldn’t give your password to other websites, and they shouldn’t ask for it.
I like OAuth, but the website (e.g. LinkedIn) still has to choose an appropriate “scope”. For instance, if they’re talking to GMail, they should just ask for permission to look at your contacts, not your calendar or messages. (All the valid scopes for Google are defined here.) This comes back to the same basic principle: if you limit how much an application is allowed to do, you also limit how much damage it can do.
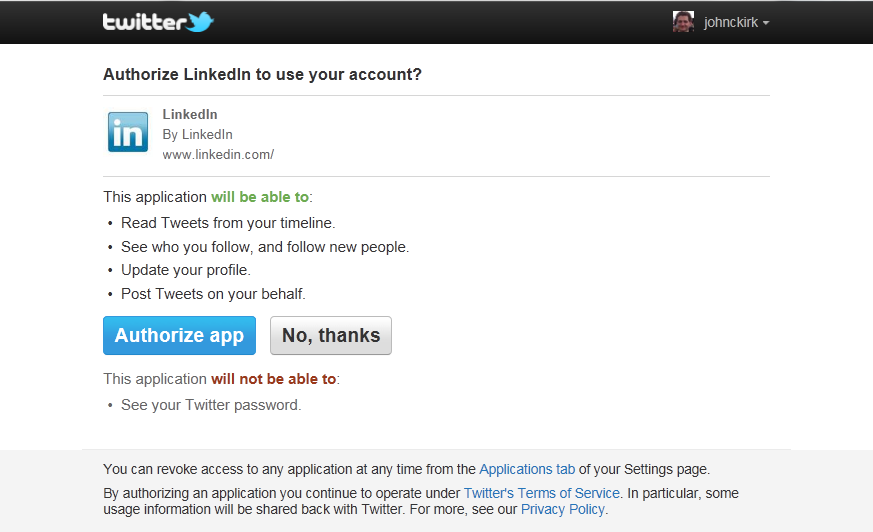
When you edit your profile on LinkedIn, you can list your other websites, e.g. a blog. They treat Twitter as a special case, so you get an OAuth prompt:
If I click “Authorize app”, LinkedIn will be able to do various things. Some of these are harmless enough; for instance, all my tweets are public, as is the list of people that I follow. However, I’m less happy about LinkedIn posting tweets on my behalf or signing me up to follow new people.
This is similar to installing an app on Facebook. Yesterday I saw an update from one of my friends (on Facebook and Twitter) that said “I just bought (something) on StarDoll. Check out my suite!” StarDoll looks like a computer version of Barbie, and there’s a sample suite here. (I found that by searching Twitter for “Stardoll” and clicking the most recent tweet.) My friend has now deleted the message from both places, so I assume that she didn’t intend to advertise this to the world. However, if you give programs permission to post as you then don’t be surprised when they use it.
I’m willing to list my Twitter account on LinkedIn (i.e. type in the website address), but I’m not willing to authorize LinkedIn to speak on my behalf. Since they clearly know about OAuth, it’s curious that they didn’t use it to gather contact data. The fine line between malice and incompetence is increasingly hard to spot.
Ultimately, I think the most important thing is knowing when to say “bog off”. Just because a website (or any other computer program) asks you for a password, you don’t have to provide it. Similarly, just because it asks you to authorise something, you don’t have to click “Yes”.
Leave a Reply