Since my email address is public, I get a lot of spam: typically 100 messages per day. The Outlook 2003 Junk E-mail filter does a decent job of catching most of it, but there are still some that slip through; I also keep an eye on the spam folder itself, in case of false positives. Generally speaking, these messages fall into three categories:
a) Direct sales for dodgy stuff, e.g. pirate software and viagra pills. (I have no idea whether they actually send the relevant goods to people who type in their credit card details, or just take the money and run.)
b) Phishing sites, e.g. “this is your bank/PayPal/Ebay, please log in via this link to confirm your details”. (If you log into their fake site, they can then impersonate you at the real site.)
c) Viruses, typically either an attachment or a link to a website with dodgy pop-ups. Sometimes there are messages which try to exploit security bugs (by effectively being a web page themselves), but these seem to be rarer.
In all three cases, the spammers want you to open the email, and I am vaguely interested to see how quickly they respond to current events. For instance, one of my junk messages today had the subject line “Anna Nicole’s cause of death still a mystery” (referring to the death of Anna Nicole Smith last Friday). On the flipside, I do get legitimate messages from strangers (“fan mail”) which tend to resemble spam, e.g. a blank subject line and an HTML formatted message.
Anyway, these messages seem to follow trends (presumably when lots of people buy the same template and list of addresses), and I’ve noticed a lot of recent messages claiming that I have an e-card waiting for me at American Greetings. I’ve been ignoring these, on the basis that they don’t include my name or any kind of personal message, so they’re unlikely to be from anybody I know, and therefore they’re likely to be dodgy. In particular, I apparently received 10 Valentines e-cards today, but I was rather sceptical about their authenticity! However, I was mildly curious to see what the con was; my computer is pretty well locked down, so I figured that I could play crash test dummy to see what happened.
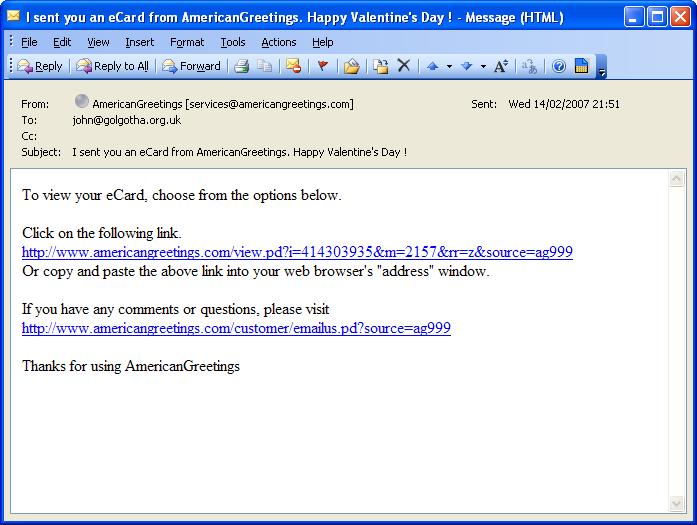
A typical email would look like this:
Leaving aside the lack of personal info, let’s look at the domain. I gather that AmericanGreetings is actually a real company, although I’ve never properly heard of them (presumably because I’m not American). They do have an official website at:
http://www.americangreetings.com/
where you can send e-cards to friends.
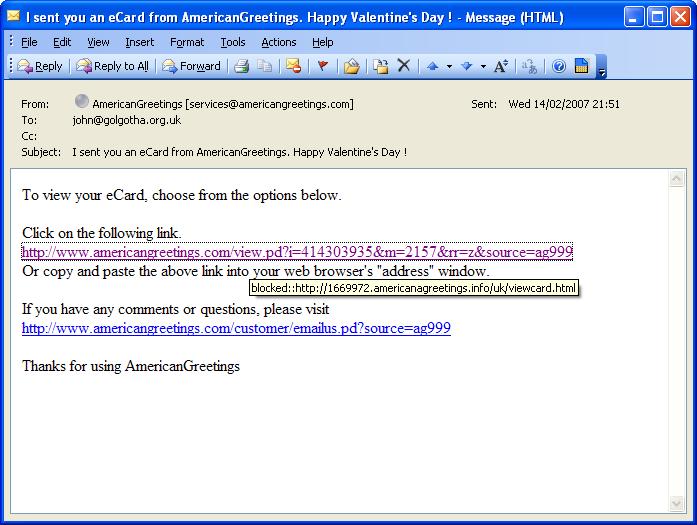
This is the same domain that the email uses, both in sender address (services@americangreetings.com) and in the hyperlinks that you can click on. Or so you might think… If I hover over one of those links, a different picture emerges:
You can’t see my mouse pointer in this image, but I’m hovering over the top link, and the tooltip shows the real address that it links to. More specifically, the domain it’s actually using (the bit after http:// and before the next “/”) is 1669972.americanagreetings.info. (I’m deliberately not including a clickable link here, to avoid any accidents.)
Looking at today’s messages, there seem to be four main domains in use:
americanagreetings.net
americansgreetings.net
americanagreetings.info
americansgreetings.info
Each of these has a random set of letters/numbers at the start (e.g. “1669972”) in the example above, and I assume that these are used to track the individual emails, so that they know which ones have been successful at luring people in. (As I say, I get plenty of spam already, so I doubt that this experiment will cause any significant increase for me.)
This is a useful sanity check with any unsolicited email that you receive – if the domains don’t match then you should be suspicious. However, if the domains do match, that doesn’t necessarily mean that the message is ok; I’ll come back to that in a few minutes.
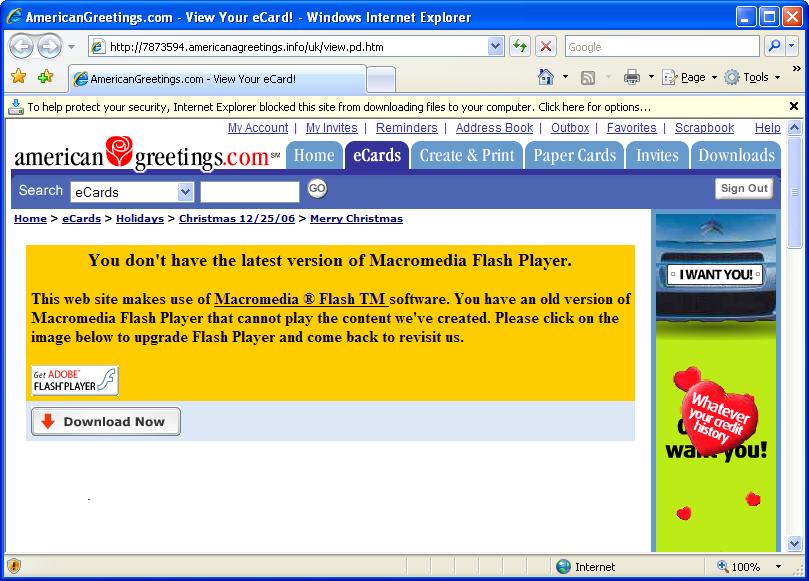
If I click on one of these links, I get taken to a web page like this:
Again, this doesn’t look too bad at first glance (aside from the dodgy domain name): it’s certainly plausible that an e-card website would use a Flash animation, and it’s possible that Adobe have brought out a new version of the plug-in since you last installed it. I’d say that Adobe are a trustworthy company, so I’d be happy to install a new version of their software. But wait, what’s this?
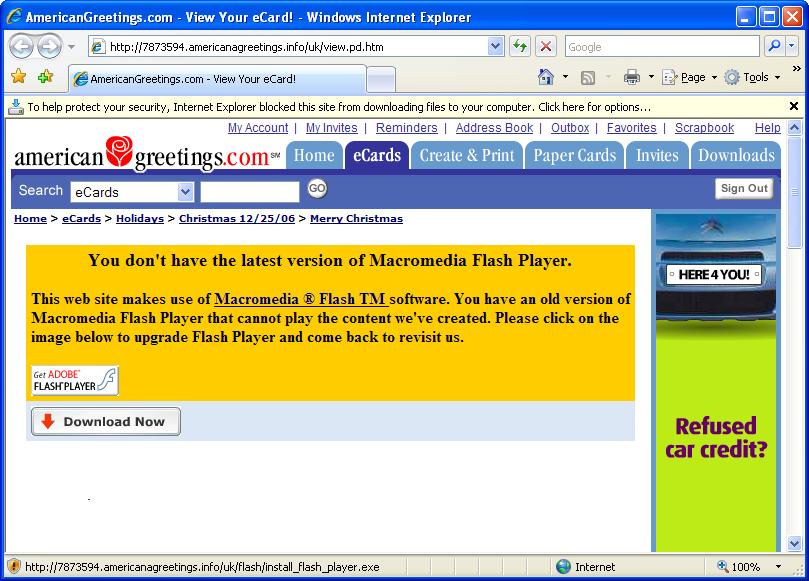
I’m doing the hover test again; sorry that you can’t see the mouse pointer, but this time I’m hovering over the image that says “Get ADOBE FLASH PLAYER”. The important bit here is the status bar, in the bottom left corner of that screenshot, since this shows me the target of the link. In other words, if I clicked on the picture (rather than just hovering over it), the status bar is telling me where I’d go to. In this case, I’d be downloading the file “install_flash_player.exe” from this website, not from the Adobe website. The key point here is that even if this was the real AmericanGreetings website, they still shouldn’t be hosting their own copy of the setup program: you should only get that from the company that actually made it.
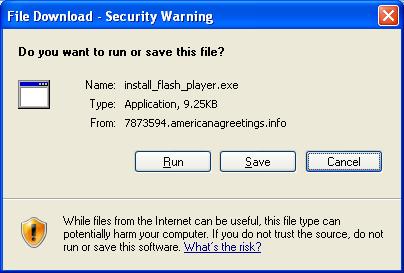
Meanwhile, Internet Explorer 7 has given me some protection here, as you can see from the info bar at the top of the screen. Basically, as soon as I loaded up that website, it tried to download a copy of the setup program to my machine, but IE7 blocked that. In the interests of testing, I told it to download the file, and it came up with the following dialog box:
This is asking me whether I want to run the program (installing the software), save it somewhere on my PC, or cancel. Since I’m not completely reckless, I chose the “Cancel” option! You will notice that this dialog box also shows you the source of the file i.e. that it’s coming from the website I’m looking at rather than the Adobe site (as explained above).
The problem here is the “dancing pigs” scenario. I’ve noticed that people often translate messages in their heads, probably without consciously being aware of it; for instance, if you are running for a train, and the person on duty says “This train is about to depart, please stand clear of the closing doors”, that internally becomes “Run faster, then you can jump in before the doors close!” In the case of a dialog box like this, it’s basically saying “Do you want to see the e-card or not?” You’ve been promised that there will be a funny video (possibly involving dancing pigs), and computers are always sticking up error messages about one thing or another, and you’re a busy person who doesn’t have time to read them all, and they’ll just be jibber-jabber about memory address 38B4 anyway, so give me my e-card!
If you do actually run the program, you’ll be in trouble; don’t rely on a virus scanner to protect you. Different programs will do different things, but the chances are that none of them will be good for you. One interesting example I came across last year involved some indirect phishing, by redirecting people to a fake banking site even when they typed in the real website address; it did this by modifying the Hosts file. A friend of mine also got into trouble when his dial-up internet connection was modified to use a premium rate number rather than his local ISP, and he didn’t find out until the (expensive) phone bill arrived. Basically, if you run a program then it can do anything that you can do; if you’re an administrator then the program can make significant changes to the way your computer works, without your consent. I strongly recommend logging in as a limited user for everyday tasks; this is an example of why that provides a useful safety net. It is a hassle to have to switch accounts each time you install new software, but if you can’t install anything at all then you can’t install anything bad.
If you do want to send someone an e-card, I’d recommend that you go to a reputable website where the card is just a data file (not a .exe file). It would also be a good idea to include some details to let the recipient know that it’s really from you, and one way of doing this is to put your email address into the website (as the recipient). You can then forward on the details to the other person, and if it turns out to be a spam trap then you’ve only compromised your own address, not your friend’s.
Leave a Reply